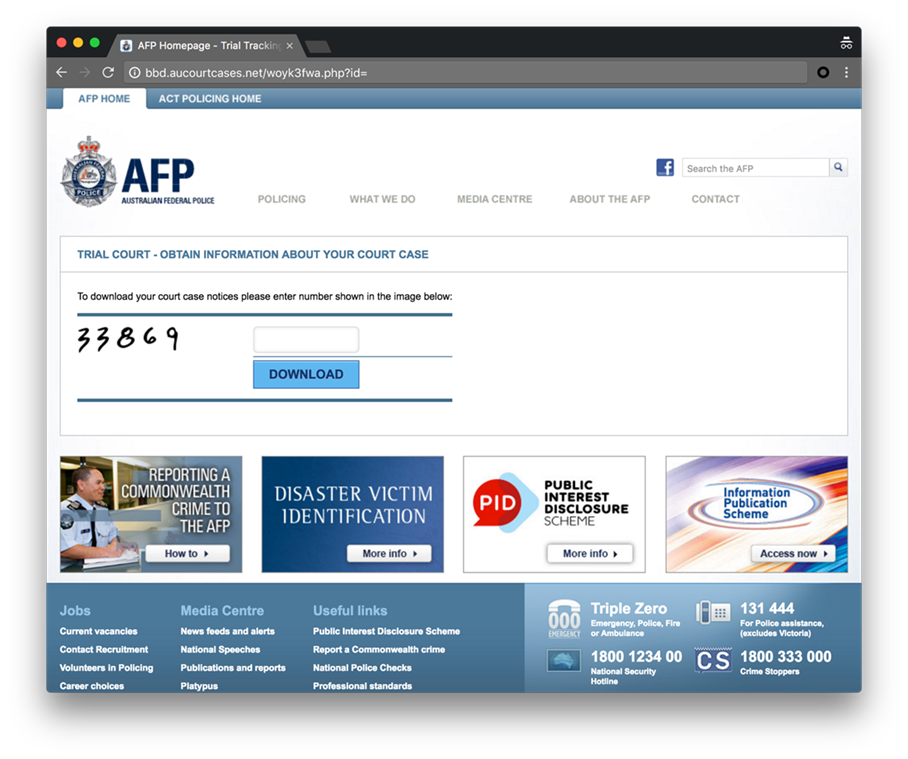
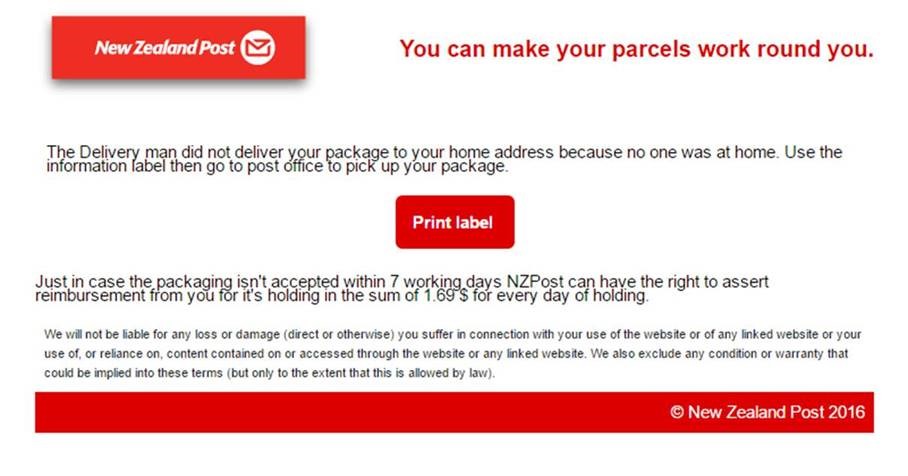
Between April and August 2016, The Australian Federal Police, Australia Post, and New Zealand Post have been among several organisations across 22 countries that have been targeted by TorrentLocker, a crypto-ransomware that spreads via spam messages, according to ESET researchers.
Between April and August 2016, The Australian Federal Police, Australia Post, and New Zealand Post have been among several organisations across 22 countries that have been targeted by TorrentLocker, a crypto-ransomware that spreads via spam messages, according to ESET researchers.
TorrentLocker displays a page claiming that a “document” (purportedly a bill or a tracking code) should be downloaded. If the malicious “document” is downloaded and opened by the user, TorrentLocker is executed. The download, ransom and payment pages are highly localised, using the user’s own language and currency.
About TorrentLocker
TorrentLocker, first analysed by ESET in 2014, is a crypto-ransomware family spreading via spam email messages and impersonating local postal services, energy or telecom companies, and more. Back then, the name used in TorrentLocker’s ransom note alert was the well-known “CryptoLocker”.
ESET researchers looked at new samples in the past months to check the state of the malware family. They discovered TorrentLocker is still active due to how it chooses its potential victims with targeted spam, and that it avoids the attention more prominent crypto-ransomware receives.
A well-known feature of TorrentLocker is how localised the download, ransom and payment pages are. Victims are provided with information in their own languages and in their local currency.
Modifications in the recent TorrentLocker variants address the mechanisms protecting internet users in selected countries, i.e. the way TorrentLocker contacts its Command-and-Control servers, protection of the C&C server by an additional layer of encryption, obfuscation and the process of encrypting the users’ files.
“These newer TorrentLocker variants have really upped the ante,” commented Nick FitzGerald, ESET Senior Research Fellow. “Earlier variants, just like other crypto-ransomware, encrypted files of specific types, as determined by their filename extension. The recent variants turn that approach on its head, encrypting all files except for a few types necessary to allow the system to keep working after the file system has been encrypted. This new approach to encrypting nearly all files on a system will have ramifications for the kind of backups needed to properly restore a system that has been encrypted by TorrentLocker.”
How TorrentLocker works
TorrentLocker is being distributed via email messages linking to a webpage and claiming that a “document” (purportedly a bill or a tracking code) should be downloaded. If the malicious “document” is downloaded and opened by the user, TorrentLocker is executed. It starts its communication with the C&C server and encrypts the victim’s files.
Recent TorrentLocker campaigns have localised webpages for 22 countries worldwide. Some examples of TorrentLocker impersonations between April and August 2016 have used major Australian and New Zealand organisations such as Australia Post, the Australian Federal Police and New Zealand Post as lures in their spam to catch their potential victim’s attention (see screenshots in the appendix).
“As always, unexpected offers, and especially claims of criminal behavior, received via email should be treated with great skepticism,” FitzGerald advises. “Should you have been expecting such an email anyway, rather than clicking the links in the email, enter the homepage address of the organisation in your browser’s address bar, or visit it via one of your own bookmarks, and follow the options provided at the site to locate your reputedly ‘missing’ parcel, ‘unpaid fine’, etc using the apparent reference number from the email.”
For more details on TorrentLocker, visit We Live Security.
Commentary from Nick FitzGerald, Senior Research Fellow at ESET
To protect yourself and avoid being infected by ransomware, including TorrentLocker, follow these 11 tips:
- Always back up your data. If you have conducted regular backups, you will be able to restore what is lost. Ensure that at least one set of backups is not connected to your computer during normal operations.
- Show hidden-file extensions. If you see an extension with “.docx.exe”, there’s something wrong with the file. Showing the extensions makes it easier to spot malicious files.
- Filter EXEs in email. If you receive an email with .EXE files, get your email to filter the executable files or only use ZIP files with password protection if you are using .EXE files.
- Disable files running from AppData/LocalAppData folders. There are rules within windows to disallow a particular, notable behaviour used by Cryptolocker, which is to run its executable from the App Data or Local App Data folders.
- Disable Remote Desktop Protocol. If you do not require the use of RDP, you can disable RDP to protect your machine from Filecoder and other RDP exploits.
- Patch or Update your software. This will ensure you’re protected from the latest threats.
- Use a reputable security suite. Having both anti-malware software and a software firewall will help you identify threats or suspicious behavior.
- Disconnect from WiFi or unplug from the network immediately. If you are being infected by ransomware, disconnect from your network immediately.
- Use System Restore to get back to a known-clean state. Make sure that you also have removed executables files as some might still be present on the system.
- Set the BIOS clock back. While most ransomware is generally set to 72 hours before raising the price, you can save time by setting the BIOS clock back to a time before the 72-hour window is up.
- Do not pay the ransom. There’s no guarantee your data will be released or properly decrypted.
“Ransomware is very active in Australia and New Zealand and will be increasingly targeting users moving forward. Users shouldn’t panic when encountering these kinds of situations and follow best practices to retrieve their data. Proactive prevention and protection can significantly reduce the risks and impact of malware and ransomware attacks,” concluded FitzGerald.
About ESET
Since 1987, ESET has been developing award-winning security software that now helps over 100 million users to Enjoy Safer Technology. Its broad security product portfolio covers all popular platforms and provides businesses and consumers around the world with the perfect balance of performance and proactive protection. The company has a global sales network covering 180 countries, and regional offices in Bratislava, San Diego, Singapore and Buenos Aires. For more information visit www.eset.com or follow us on LinkedIn, Facebook and Twitter.
Appendix