A special cybersecurity luncheon held in Sydney this week highlighted the disconnect between the Corporate C-Suite and Corporate IT Departments. BAE Systems partnered with the Australian British Chamber of Commerce to review and highlight their recent report ‘The Intelligence Disconnect: The 2017 Cyber Defence Monitor Research’. Held in the swish, high-rise offices of lawyers King & Wood Mallesons, offering vast, inspiring views across Sydney, it would seem this is the best and potentially, the only setting to capture the attention of corporate executives.
A special cybersecurity luncheon held in Sydney this week highlighted the disconnect between the Corporate C-Suite and Corporate IT Departments. BAE Systems partnered with the Australian British Chamber of Commerce to review and highlight their recent report ‘The Intelligence Disconnect: The 2017 Cyber Defence Monitor Research’. Held in the swish, high-rise offices of lawyers King & Wood Mallesons, offering vast, inspiring views across Sydney, it would seem this is the best and potentially, the only setting to capture the attention of corporate executives.
Alex Taverner, BAE Systems’ Head of Cyber JAPAC for the Commercial Services division, highlighted that the C-Suite and IT decision makers expect and indeed, are likely, to see an increase in volume and sophistication of cyber-attacks in 2017.
To compile the report, BAE Systems commissioned strategic insight analysts, Opinium to undertake research to understand the current state of play when it comes to business cyber security. A total of 221 C-suite and 984 IT Decision Makers were polled to understand their concerns and perceptions of preparedness when it comes to their own cyber security.
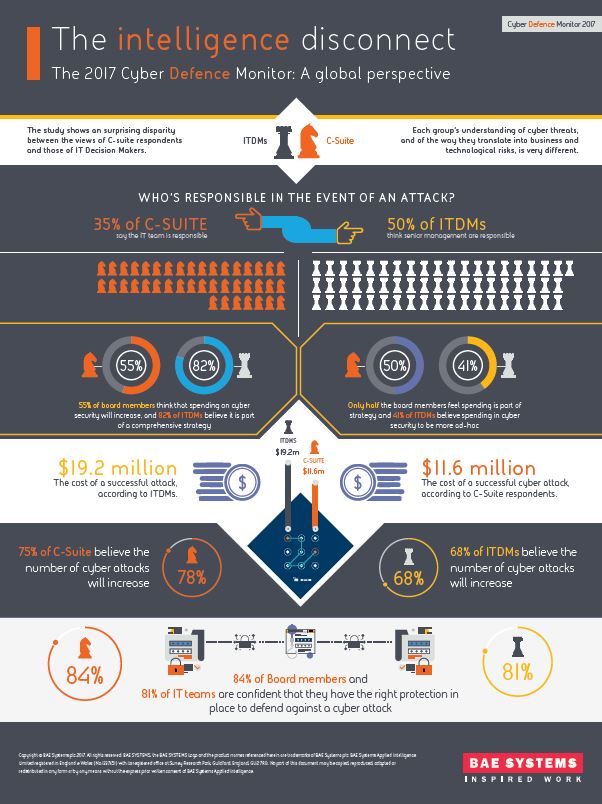
The research disclosed that the C-suite level, estimate the cost of a successful attack to be dramatically lower than their IT colleagues. IT Decision Makers believe the cost of a successful cyber-attack on their business to be around US$19.2m compared to an estimation of just US$11.6m from C-suite. In addition, while 82% of IT teams report that their cyber security spend is part of a comprehensive strategy, only half of the C-suite (50%) believe this to be the case.
In the luncheon panel, moderated by Roger Wilkins AO, Member of the Board of the Forum of Federations and former Secretary of the Attorney-General’s Department, Alex Taverner was joined by Cheng Lim, Partner and Leader of the Cyber Security initiative at King & Wood Mallesons, Stuart Mort, Director of Cyber Security, Optus, Dr Sally Ernst, Co-Founder of the Australian Cyber Security Network and Daryn Wedd, General Manager, Technology Security and Governance, ASX.
The group discussed the defining challenges faced by Australian businesses grappling with cyber security and how Australian businesses compare globally in their concerns and perceptions of preparedness when it comes to their own cyber security.
Stuart Mort of Optus highlighted at the outset that the first data breach reporting legislation was introduced in California in 2002, into Europe in 2009 and in 2017, only now, has Australia finally introduced this legislation. An interesting side note was Roger Wilkins confirmed statutory tort law was considered in 2012 for cyber negligence, but not proceeded with.
“It seems Australia is playing catch-up”, Stuart Mort identified. “Organisations need to have the security function in the right place in the organisation and it now should have its own line of business, allowing it to work with physical security, human resources and finance. With Australia playing catch-up there is still a need for structural change to get cyber as a board level issue.”
Sally Ernst proposed the concept of calling for a moratorium for companies implementing ASD’s Essential 8 to open up the ability for corporates to collaborate and share information without concern of compliance breaches and to facilitate learning and leveraging the current security postures companies already have.
Daryn Webb stated security is like any other business unit. It needs a strategy, defined plan and a clear roadmap. “Nothing replaces a well-informed plan and strategy that talks to the maturity of the organisation. Security is bidding for scarce funds and scarce resources, like all other business units. Measure the plans by testing with penetration tests, red teaming, response, internal vulnerability assessments and talking to peers and colleagues.”
There is also the importance of protective security with the human aspect and social engineering, year old concepts that are designed for manipulating individuals. Stuart Mort asserted, “We often talk about the technology risk but the number one risk is the human element and one of the first places of weakness is social engineering. The ability to be able to pick up the phone and manipulate an individual and get information out of them. It is year old concepts used by intelligence agencies and the computer underground are damn good at it.”
“So, before they have gone anywhere near the technology concept they have targeted a human. We need to have an overarching security umbrella that can work with human resources. We need to work with them in terms of comprehensive security education awareness and that takes us away from a technology theme. This is where security needs its own line of business to work across the organisation. Organisations need to integrate more physical and cybersecurity, Stuart said, “It is the building security systems, the cameras are all traveling across our networks now so we need to understand them. So, if we’re doing compliance or ethics investigations we need to be able to pull data from across the technology environment, including physical systems and be able to tie them together. It just reinforces my point that we need to look at security holistically.”